I had a user this week call me complaining that Microsoft Edge would freeze on launch and then crash and close. After investigating her event logs it was determined the faulting module was emodel.dll
Faulting application name: MicrosoftEdge.exe, version: 11.0.16299.371, time stamp: 0x5abdaed4
Faulting module name: EMODEL.dll, version: 11.0.16299.371, time stamp: 0x5abdaf79
Exception code: 0xc0000409
Fault offset: 0x000000000018bcae
Faulting process id: 0x2900
Faulting application start time: 0x01d3e794d12ebc95
Faulting application path: C:\WINDOWS\SystemApps\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\MicrosoftEdge.exe
Faulting module path: C:\WINDOWS\SystemApps\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\EMODEL.dll
Report Id: 560abf0f-e6c8-4b45-8b96-d448f9aa934d
Faulting package full name: Microsoft.MicrosoftEdge_41.16299.371.0_neutral__8wekyb3d8bbwe
Faulting package-relative application ID: MicrosoftEdge
I have not seen this error before and there were no other users in the environment experiencing this issue. My first troubleshooting step was to see if there were any unique applications that were specific to this user.
This particular user is the CFO of the company and logs into a number of banking websites. To enhance security many banks force customers to download additional software to supplement logins in order to prevent intrusion and hack attempts. This user was using a product from IBM
IBM Trusteer Rapport & Microsoft Edge EMODEL.DLL
Continue reading “Microsoft Edge Crashes On Launch – Faulting Module EMODEL.DLL”
 When cleaning equipment I like to use as mild a cleaner as possible and work my way up to something stronger if necessary. I find automotive products to be very mild and since I’m always cleaning and polishing my cars I have many different types of cleaners at my disposal.
When cleaning equipment I like to use as mild a cleaner as possible and work my way up to something stronger if necessary. I find automotive products to be very mild and since I’m always cleaning and polishing my cars I have many different types of cleaners at my disposal.





 I’m Joe hacker and I have just installed malware on one of your employees workstations. I have quickly gained access and I am now able to execute code and commands. What is the first thing I’m going to do? If you said start poking around you would be correct. After I look for anything of value on my host computer I will quickly begin scanning the subnet looking for hosts that are alive. I will also begin mapping the network for services that are possibly vulnerable to attack. This is where the Honey Pot fits in. It has been patiently siting on your network waiting for someone to direct a packet of data in its direction and alert you to possible trouble.
I’m Joe hacker and I have just installed malware on one of your employees workstations. I have quickly gained access and I am now able to execute code and commands. What is the first thing I’m going to do? If you said start poking around you would be correct. After I look for anything of value on my host computer I will quickly begin scanning the subnet looking for hosts that are alive. I will also begin mapping the network for services that are possibly vulnerable to attack. This is where the Honey Pot fits in. It has been patiently siting on your network waiting for someone to direct a packet of data in its direction and alert you to possible trouble.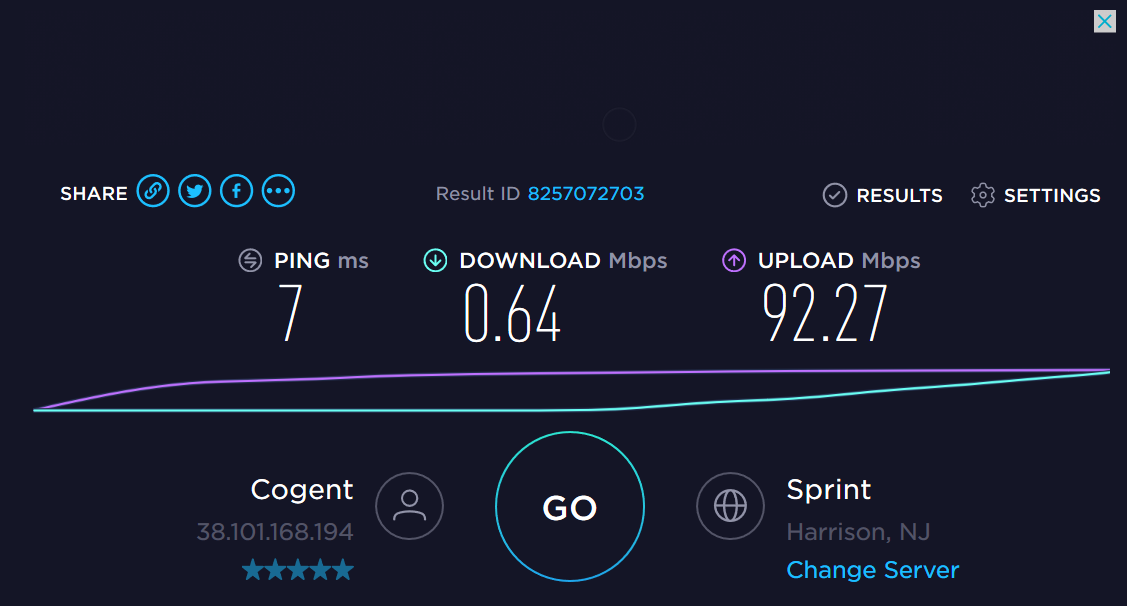
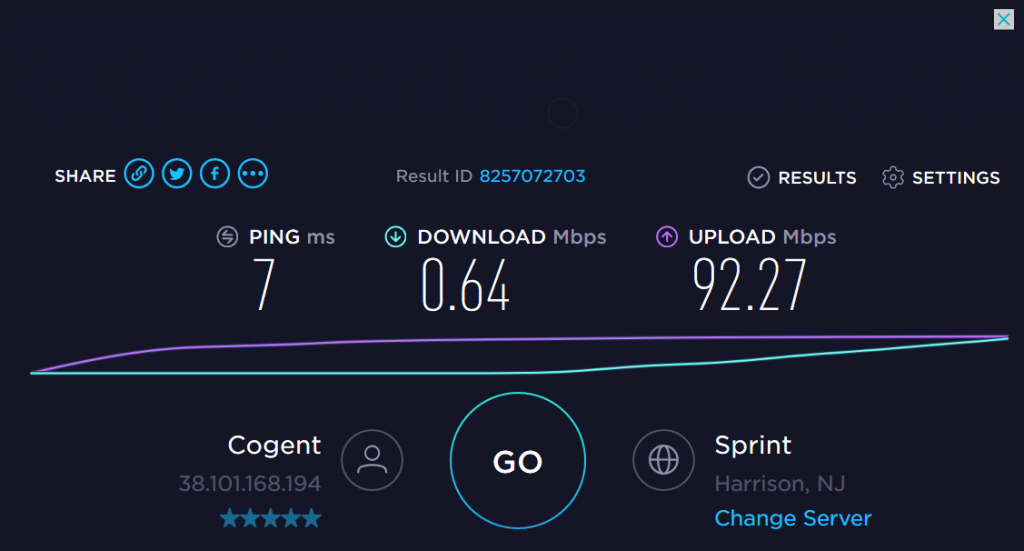






 The first time I saw this attack I was taken back for a moment because the password in the email was REAL. It was actually one of my “throwaway” passwords and kind of freaked me out.
The first time I saw this attack I was taken back for a moment because the password in the email was REAL. It was actually one of my “throwaway” passwords and kind of freaked me out.


