One of the dreaded jobs of the Sys. Admin is getting the call, I’m locked out. Its the same call every time:”I don’t know what happened, I’m just locked out.” You say something to the effect of, “Did you forget your password? Did you type it in wrong? Caps lock on?” No matter what the case wouldn’t it be nice to know a user was locked out before they called you. Plus it would be great to know if someone was hacking away internally or externally at your network.
Passwords Are Important.
First and foremost you should be subjecting your users to some type of lockout policy. In my organization I give you 3 chances to get it right and then a 20 minute waiting period. This at least will slow down the brute force hacker. Furthermore you should have some type of password policy in place. The old standard was:
Complex Passwords
- 8 Characters or more
- Letter (Upper / Lower)
- Number
- Symbol
- 90 day expiration
I still believe 100% you should have COMPLEX passwords for all your users, however in recent years I have been undecided about the 90 day expiration. My theory is if you make a user update their password every 90 days they are simply going to write it on a sticky and place in on their monitor. Or even dumb their passwords down by incrementing a number on the end. Password1 becomes Password2 and so on.
How to immediately detect a lockout:
If your Active Directory is configured properly, upon each lock out an event will be written to your security log. (on a domain controller) . Access the event viewer and search for Event ID 4740. These are the lockout events.
The key to being notified is monitoring the log and triggering a script when Event ID 4740 is found. We can do this for FREE using the Windows Task Scheduler. Open Task Scheduler on your Domain Controller and add the following task – Account Lockout Notification
In the General Tab – Add a description (to help you remember what it does), Also set it to “Run with highest privileges”
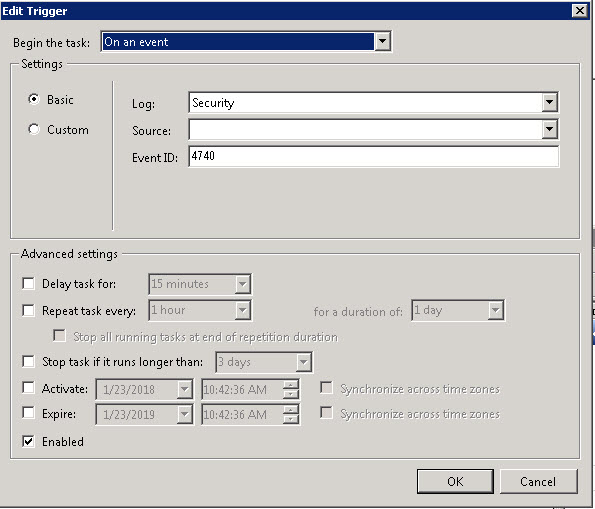
The next tab is Triggers and should look like this:
Triggers simply tells the task scheduler to look for 4740 events
The next tab is actions – this is where the magic happens. Once triggered by event 4740 we need to find the latest event package it in an email and send it to the admins. I accomplished this with a Power Shell script.
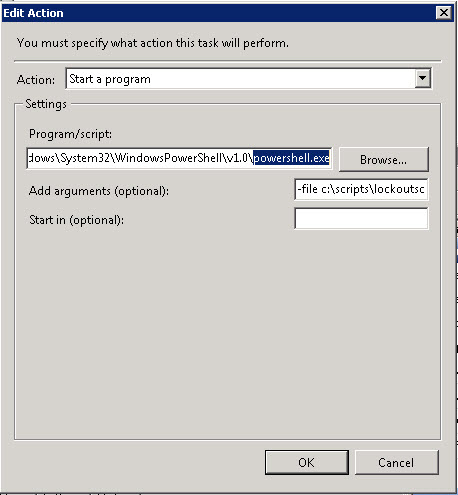
The Action is to “Start A Program”
You can run Power Shell from:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Save the script in a folder and then add it as an argument
-file c:\scripts\lockoutscript.ps1
Here is a copy of my script
######################################################### ## Check For Locked Out Active Directory Accounts ## ## ## -Sends Email Updated to Administrators ## ## -Run VIA Task Scheduler ## ## -Scan for event ID 4740 ## ## ## Joe Oiveri - V 1.0 12/18/2017 ## ######################################################### #Declare variables to be used for the Email $MailSubject= "ALERT: User Account locked out" $MailFrom="REPLY@EMAIL.HERE" $MailTo="admin1@domain.com,admin2@domain.com" #Gets the Event Log that contains the most recent lockout event $Event = Get-EventLog -LogName Security -InstanceId 4740 -Newest 1 #Creates a variable which contains the contents of the lockout event log. This is used for the actual message in the email $MailBody= $Event.Message + "`r`n`t" + $Event.TimeGenerated #Creates an SMTP Object and assigns an SMTP Address $SmtpClient = New-Object system.net.mail.smtpClient $SmtpClient.host = "mail.server.smtp.address" #Creates a new Mail Message Object. This is the object needed for the addressing email, subject, body, etc $MailMessage = New-Object system.net.mail.mailmessage $MailMessage.from = $MailFrom $MailMessage.To.add($MailTo) $MailMessage.IsBodyHtml = 0 $MailMessage.Subject = $MailSubject $MailMessage.Body = $MailBody #Actually Sends the Message $SmtpClient.Send($MailMessage)
Save the script somewhere PS can call it, and test!
That’s it! This script can be modified for any event in your log files
Just to recap –
- Event viewer logs a 4740 Event
- Task scheduler looks for 4740’s in the security log
- Calls the Power Shell Script
- Power Shell scrapes the log for the most recent 4740 and emails it to the admin
Done!
Thank you for reading my blog,
Joe