I am one of the few on the planet that still hosts my own servers in house. Sorry, but I don’t really see the benefit of moving everything to the cloud when keeping it in house allows me the control and flexibility I want. I especially like having an Exchange OWA server in house.
With that said, hosting your own systems can be troublesome as well. Maintaining the hardware, infrastructure and security are items that would get farmed out in a cloud environment. This post focuses on the security end, or rather attempting to track hack attempts.
In January, I sent up a trigger to alert me every time a user is locked out. -> Know instantly when a user is locked out <- Its a good read if you’re interested. This trigger reads the event logs, looks for the lockout event and sends the info to me via email. A great help in being proactive with my users. It also alerts me to hack attempts. Too many incorrect login attempts on OWA would trigger a lockout event. During a recent weekend, I was receiving lockout emails every 30 minutes. So who was doing this? What did they want?
How to check Exchange OWA IIS logs
In simple terms they were attempting to gain access to my mail server, so I decided to track down the hacker. (Or in this case atleast the country of origin)
In an attempt to figure out who was hacking away at my OWA instance I decided to pull the IIS logs and take a closer look. Let me tell you there is a wealth of data in Exchange OWA logs, in fact way too much data.
Step 1 – Get Log Parser 2.2 from Microsoft
Download and install Log Parser command line tool from Microsoft
Once downloaded follow the install instructions to get things moving along. Log Parser will make a start menu entry for easy launch. My install was NOT in the command path so I had to switch to C:\Program Files (x86)\Log Parser to run the commands.
STEP 2 – Find your Exchange OWA logs
Locate your OWA log files. Not sure where they are?
- From the Windows Start menu, hover over Administrative Tools and click on Internet Information Services (IIS) Manager.
- In the lefthand tree view, expand the server name’s folder and click on the Sites folder to load a list of sites in the content pane. Make note of the desired site’s ID.
- Double click on the site to open its settings in the content pane. (Alternatively, you can expand the Sites folder and click on the site name in the lefthand tree view.)
- Select Logging from the content pane to load the Logging settings. In the Directory field, you’ll find the path in which your logs reside.
- Navigate to the LogFiles folder by following the path contained in the Directory field.
- Within the LogFiles folder you’ll find a subfolder for each site configured in SmarterStats, labeled as W3SVC1, W3SVC2, etc. The last number in the folder name corresponds to the SiteID. For example, W3SVC1 would contain the logs for the site with ID 1 in IIS. Find the folder that matches your site’s ID and you’ve found its location path.
** TIP – You may want to keep you IIS log files on a different drive other than C:\ they can become quite large and take up a hefty amount of disk space over time
STEP 3 – Parse the log for IP addresses
You are now going to search the log file for unique ip addresses with this command.
logparser.exe "SELECT DISTINCT date, c-ip INTO d:\temp\output.txt FROM d:\temp\u_ex180918.log" -i:W3C -o:W3C
Make sure you define and output path and file to put the results of the parse.
The file that is generated will have all the unique IP addresses that attempted to access your Exchange OWA site. I pulled the file into excel and sorted the IP addresses. Then I removed any internal 10.x.x.x addresses or known addresses.
STEP 4 – Who owns these IP addresses
After step 3 you are left with a long list of random IP addresses, lets see if we can Geo Locate them to get an idea of where the traffic is coming from.
This on line tool – Bulk IP to location lookup is rather slow, but gets the job done for 500 IP addresses at a time!
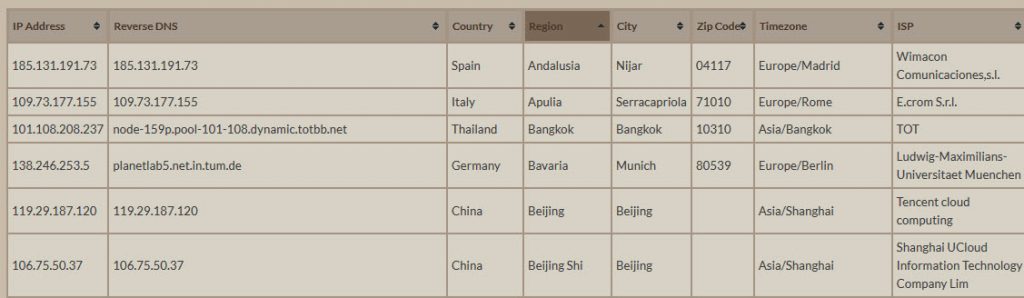
The resulting file can be pulled into Excel for further investigation, feel free to sort the list by county to get a better idea of whats going on.
STEP 5 – How many times have they attempted to login?
Now we have a nice list of IP addresses and countries of origin, but we don’t know how many times each IP had attempted a connection.
logparser "select c-ip, count(c-ip) as requestcount from d:\temp\u_ex180920.log group by c-ip order by count(c-ip) desc" -rtp:-1 > d:\temp\count20.txt
The above Log Parser 2.2 command scans the log file again displays the number of hits for that log.
I used a weeks worth of log files to determine the number of hits and frequency an IP address was attacking the server. Then I blocked the worst offenders at my firewall. I also used the Geo blocking feature in my firewall to block countries I don’t do business with.
SUMMARY
Log Parser is a great FREE tool to manipulate your IIS log files into easy to read data. The best part is the tool is free from Microsoft.
I also can’t stress enough that you should be running 2 factor authentication on your Exchange OWA install for added protection.
Thank you for reading my blog,
Joe