I had a couple of users in the office this week attempt to enable word macros on a document they received in email. I try to give my users as much information as I can to avoid viruses and malware, but each week the hackers come up with additional methods to attempt unauthorized network access.
Exploit Vector:
This time around the hack was email based and the email came from a known source. The attacker has already gained control of the senders workstation and had sent the message as a reply to an earlier thread.
Example:
- Client sends me a legitimate message:
TO: Joe@xyz.com
FROM: Sam@abc.com
SUBJECT: Business Dinner
BODY: Joe can you come to dinner tonight
- I reply to client
TO: Sam@abc.com
FROM:Joe@xyz.com
SUBJECT: RE:Business Dinner
BODY: Sorry can’t make it————
TO: Joe@xyz.com
FROM: Sam@abc.com
SUBJECT: Business Dinner
BODY: Joe can you come to dinner tonight
- Hacker now intercedes in the email threadTO: Joe@xyz.com
FROM: Sam@abc.com
SUBJECT: RE:Business Dinner
BODY: I have a proposal for you. Please see attached and confirm.
———————–
TO: Sam@abc.com
FROM:Joe@xyz.com
SUBJECT: RE:Business Dinner
BODY: Sorry can’t make it————
TO: Joe@xyz.com
FROM: Sam@abc.com
SUBJECT: Business Dinner
BODY: Joe can you come to dinner tonight
As you can see for the above interaction, the firs two messages in the email thread are legitimate and then the hacker inserts a second reply with the attached Word document and virus payload. This would indicate the hacker has full control of the users PC. Also after reviewing the email message headers, it was clear that the sending server was the originators server.

Viral Payload:
The intent of this attack is to have a user open a Word document and execute the macros launching the viral payload. Word has become more secure over the years and now requires user intervention to “Enable Macros” I can’t stress enough unless you are 100% sure or created them yourself, macros are almost always BAD! Don’t do it.
Below is what the Word Document looks like
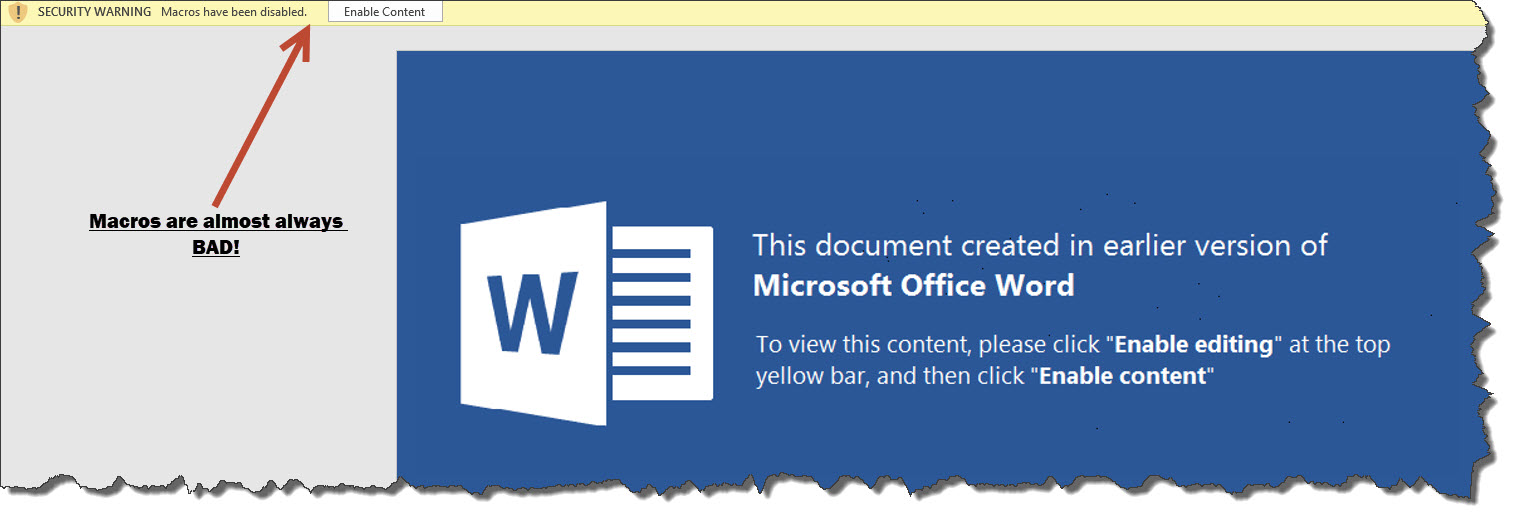 If you made it this far you’re not paying enough attention to your email messages. However there are some hints here that should tip you off that this is an attack.
If you made it this far you’re not paying enough attention to your email messages. However there are some hints here that should tip you off that this is an attack.
- English as a second language – “This document created in earlier version of…”
Hmm.. it should read – “This document was created in an earlier version of…” - Earlier version of Word? – Word is very backward compatible and if you have any semi-modern Microsoft Word it should be able to open the document without any prompts or extra steps
- MACROS ARE ALMOST ALWAYS BAD!
SUMMARY:
Just remember to play it safe when opening attachments in email messages. If you’re not expecting an attachment don’t open it!
Things to remember:
- Always “hover” your mouse over links in email to see where they actually go.
Try this link www.mylink.com It will take you to Amazon.com - Look for slight errors in email addresses, hackers know that many business and users have SPF records (sender policy framework) that can check if AOL or YAHOO really sent the message. To avoid this they make slight changes to the email address EXAMPLE: JOE@JOE.COM is different from J0E@J0E.COM (the “o” was changed to “0” zero.)
- Don’t open unknown attachments, or unexpected attachments especially if they contain Macros
- Keep your virus and malware protection up to date!
- If possible use a spam filter to block countries you do not expect to receive email from (Russia, China and Korea are huge sources for email attacks)
Thank you for reading my blog,
Joe


