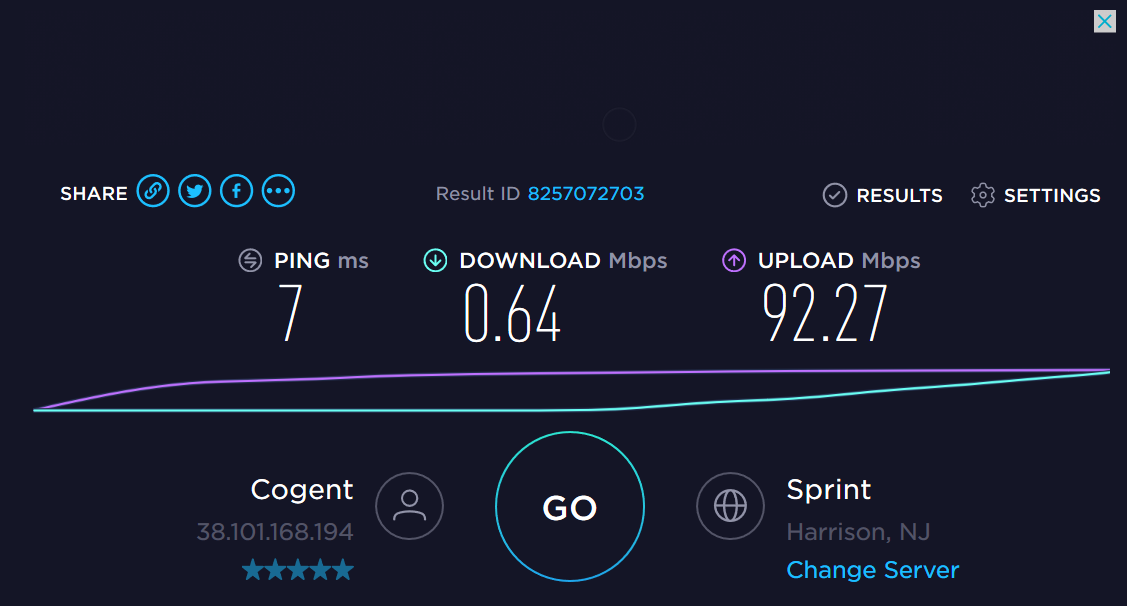
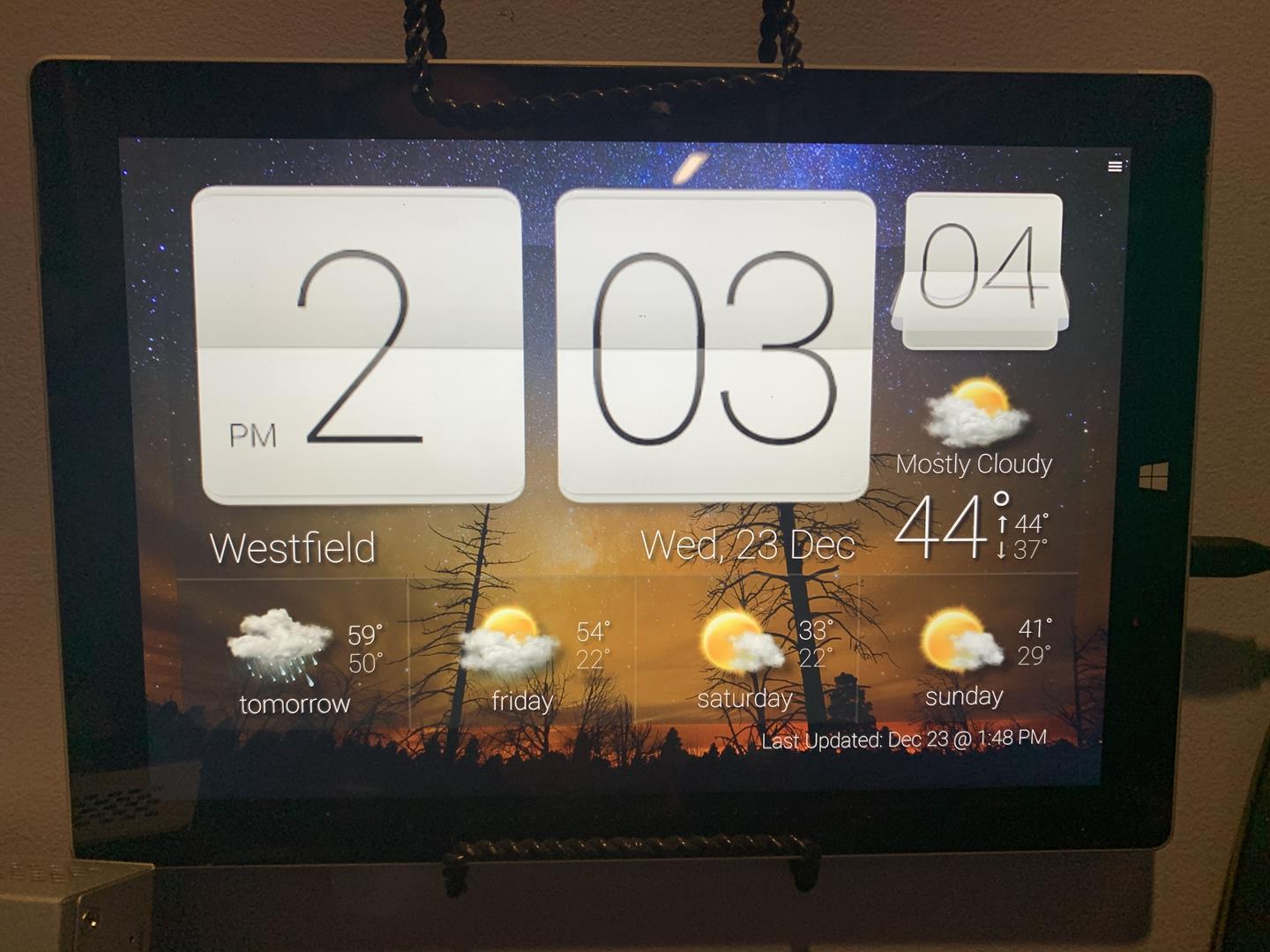
In our consume it and toss it world we tend to discard our old electronics for the faster, better newer items. I know we are pretty good at recycling our old electronics, but wouldn’t it be even better to repurpose our old gear, maybe give it a new life as something else? I had an old Microsoft Surface 3 sitting on my desk collecting dust for a while. The specifications were pretty weak. 4GB of RAM, 64GB disk, and a really slow mobile processor. Compared to today’s standards its barely enough to run Windows 10, at least the disk was SSD.
What I did with my Microsoft Surface 3
Looking at the Surface I saw a great opportunity to make a wall clock weather station! With just a few prep steps and a neat low cost trick to mount the surface to the wall I had this project done in under an hour.
Continue reading “Microsoft Surface 3 – Repurpose, Reuse, Recycle”






 I’m Joe hacker and I have just installed malware on one of your employees workstations. I have quickly gained access and I am now able to execute code and commands. What is the first thing I’m going to do? If you said start poking around you would be correct. After I look for anything of value on my host computer I will quickly begin scanning the subnet looking for hosts that are alive. I will also begin mapping the network for services that are possibly vulnerable to attack. This is where the Honey Pot fits in. It has been patiently siting on your network waiting for someone to direct a packet of data in its direction and alert you to possible trouble.
I’m Joe hacker and I have just installed malware on one of your employees workstations. I have quickly gained access and I am now able to execute code and commands. What is the first thing I’m going to do? If you said start poking around you would be correct. After I look for anything of value on my host computer I will quickly begin scanning the subnet looking for hosts that are alive. I will also begin mapping the network for services that are possibly vulnerable to attack. This is where the Honey Pot fits in. It has been patiently siting on your network waiting for someone to direct a packet of data in its direction and alert you to possible trouble.